DNS Intelligence Detects ViperSoftX Infostealer Variant
A new ViperSoftX Infostealer variant has been uncovered by EfficientIP’s DNS Threat Intelligence. Using systematic domain generation and stealthy tactics, this malware evaded traditional defenses—until DNS-level monitoring revealed its infrastructure.
EfficientIP’s DNS Threat Intelligence has detected a new ViperSoftX Infostealer variant linked to the previously exposed EIP-458-CryptoStealer. What began as a single-domain, stealthy zero-day has evolved into a complex, well-structured, and resilient campaign designed to evade takedowns. Attackers now reinforce their infrastructure with systematic domain clusters, selective registrations, and shared configurations, making the infostealer more persistent and dangerous. This blog shows the critical role of DNS Threat Intelligence in exposing such hidden threats.
Recap: How DNS Threat Intelligence First Exposed the EIP Infostealer
The EIP-458-CryptoStealer, later confirmed as a ViperSoftX Infostealer variant, was first detected by EfficientIP’s DNS Threat Intelligence through DNS traffic monitoring. This early detection was crucial as the zero-day malware employed advanced evasion tactics, shifting from DNS TXT manipulation to HTTPS and operating in memory with encoded data to enable stealthy data exfiltration. Traditional security measures like antivirus, EDR, and firewalls proved insufficient against such stealthy threats, underscoring the necessity of DNS Security as a critical layer of defence. An EfficientIP previous blog detailed this deep research, showing how DNS Threat Intelligence uncovered the campaign and exposed its evolving tactics.
A New Variant of the Infostealer Recently Exposed
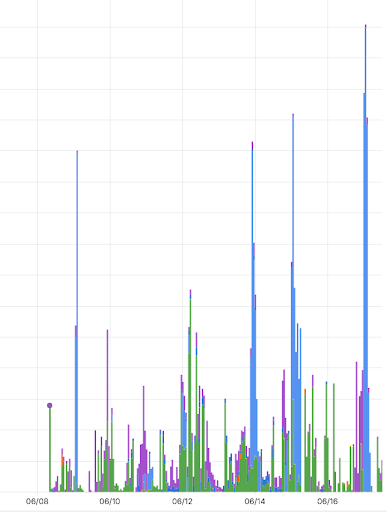
Continuous monitoring by DNS Threat Intelligence identified a new zero-day variant of the EIP-458 Infostealer campaign by mid-2025, formally designated EIP-461-CryptoStealer v2. The variant reveals that the campaign is expanding, showing greater persistence, and evolving its tactics. Moreover, the research revealed that the Cryptostealer is, in fact, a ViperSoftX Infostealer variant.
The broadened activity demonstrates that attackers are deliberately strengthening their infrastructure to resist takedown efforts. This shift highlights a determined move toward long-term durability, persistence, and reach.
Strengthening Attack Infrastructure With Structured Clusters
In analyzing this new ViperSoftX Infostealer variant, researchers found that attackers no longer relied on isolated domains. Instead, they built structured clusters with clear naming rules, rotating them in as needed. This systematic design gave the campaign persistence, even when individual domains were blocked or taken down.
We’ll cover these techniques in depth — including how EfficientIP’s AI-driven detection exposed entire clusters before they became operational — in our next blog focused on early detection of domain-based threats.
Coordinated Infrastructure and Registration Tactics
Expanding beyond domain patterns, the campaign demonstrated a carefully coordinated approach to infrastructure and registration. While hundreds of interchangeable domains were algorithmically possible, only a select few were formally registered and made operational.
Notably, activatordb.com was registered on March 16, 2025 and slimawriter.com on April 17, 2025, both through Njalla, a registrar known for providing anonymity services. In contrast, quasardb.com appeared legitimate — registered since 2007, tied to QUASAR DATABASE TECHNOLOGIES, hosted on Microsoft Azure, with ownership validated through TXT records.
The use of VirusTotal Graph quickly highlighted links across these domains. Several unregistered domains were already flagged as malicious by antivirus engines and associated with a specific PowerShell script (SHA256: db0bb352bd600db588e65f7bd1ee74bfad9cb11ee67f59497e2d442c6f962aa9). This script was responsible for downloading the stager from domains such as slimawriter.com, underscoring the operational role of this infrastructure.
To read the full article head over to EfficientIP Blog HERE