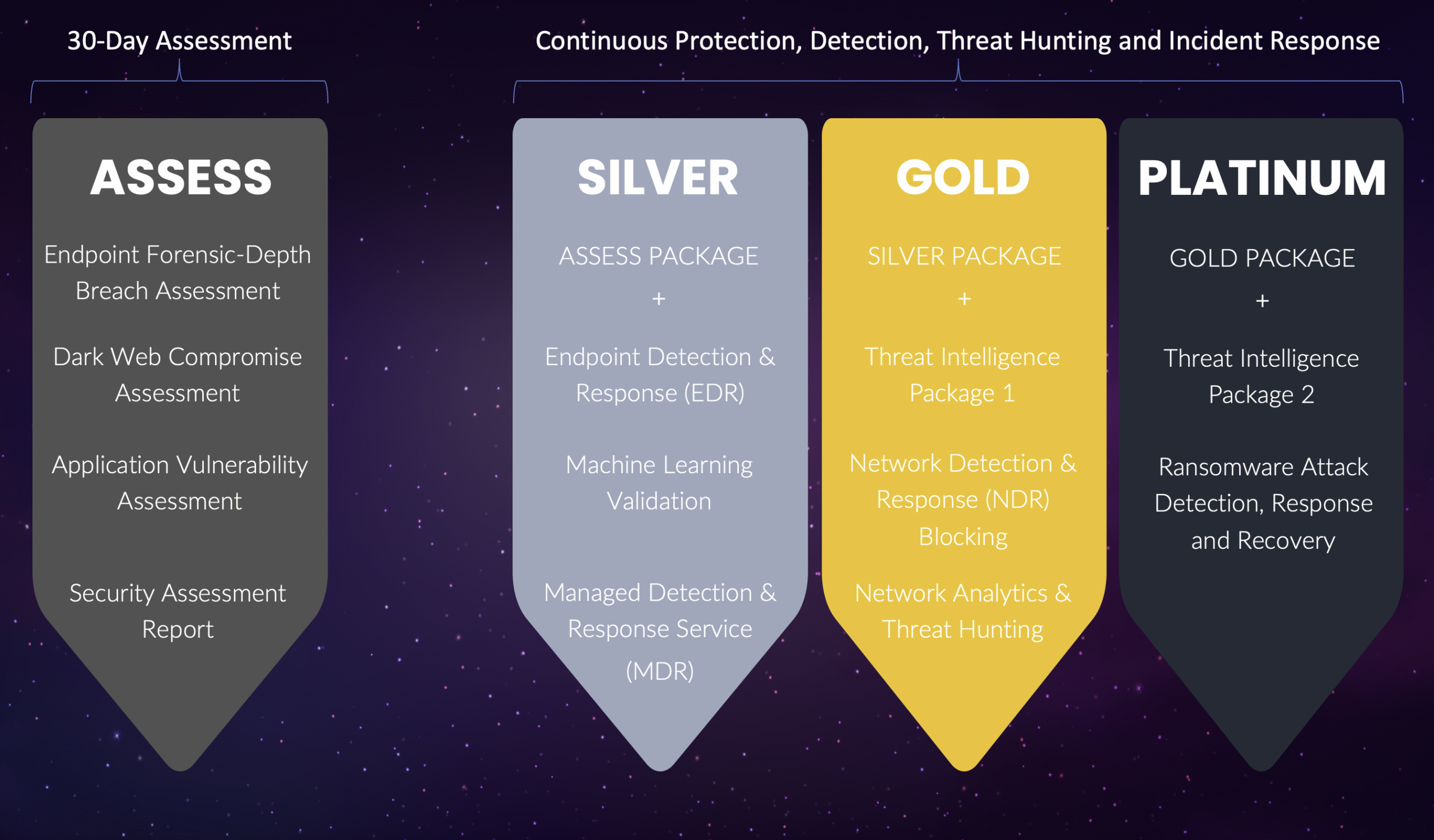
Safeguarding Business
CyberStash’s integrated and highly automated approach combines protection, advanced threat detection, proactive threat hunting, and continuous response to safeguard your on-premises, cloud and remote environments around the clock.
Organisations can elevate cybersecurity with CyberStash’s Advanced Managed Security Services. The Enhanced Threat Detection capabilities provide 24/7 cyber defence, fortifying operations against evolving threats and safeguarding company’s reputation. With CybserStash’s Proactive Threat Hunting and Incident Response, the user will benefit from a robust defence strategy that ensures timely notifications and detailed incident reports, offering transparency and empowering informed decision-making.
CyberStash is an Australian company.

MDR SERVICE
Benefits of CyberStash’s MDR Service
Fortified 24/7 Cyber Defense
Elevate your organization’s security with confidence. CyberStash’s MDR service delivers robust 24/7 cyber defense, safeguarding your company’s reputation and ensuring secure operations. Clients receive timely notifications and detailed reports on validated incidents, ensuring transparency and informed decision-making.
Validated Incident Response
Streamline operations by reducing alert fatigue. Our Eclipse.XDR Cyber Defence platform autonomously validates and prioritizes threats, minimizing false positives and boosting overall efficiency. CyberStash Security Analysts swiftly validate and respond to confirmed breaches, minimizing their impact to your business.
Optimised Resource Management
Drive innovation with optimized resource allocation. CyberStash Security Analysts manage complex security operations and incident response, empowering your team to deliver IT value and drive business success.
Progressive Exposure Reduction
CyberStash continually reduces your organization’s exposure to cyber attacks using vendor-agnostic threat intelligence. We report on adversary infrastructures and recommend proactive blocking strategies to strengthen your security posture.
Expert Proactive Insights
Boost your security with expert insights and timely advisories. Our skilled professionals monitor emerging threats and provide actionable recommendations, helping you stay ahead of risks and maintain robust protection for your business.
Enhance Compliance Alignment
Ensure compliance with industry regulations and standards. CyberStash’s MDR service helps your organization meet regulatory requirements, reducing risks associated with non-compliance and maintaining trust among stakeholders.
- Attack Exposure Reduction
- Independent Positive Validation
- Zero-Day Breach Detection
- Ransomware Defense
- Risk & Resource Optimisation
Eclipse XDR
Experience Eclipse.XDR, the groundbreaking autonomous cyber defense platform revolutionizing protection, detection, threat hunting, and incident response.
Engineered by Security Analysts for Security Analysts, Eclipse.XDR empowers an organisation with unmatched security capabilities to proactively defend against evolving cyber threats.
- Vendor Agnostic Threat Intelligence Platform
- Intelligent Blocking Gateway
- SIEM Cluster with Machine Learning
- Real-time Adversary Behaviour Detection
- Application Vulnerability and Anomaly Detection
Eclipse NDR
Network Detection and Response
An automated, predictive, actionable cybersecurity platform that protects your organization by blocking millions of cyber threats in real time.
Ultimate Protection and Maximum Throughout
Block attacks at line speeds of up to 10 Gbps. Protect on-premises and in-cloud workloads against inbound attacks that target exposed services. Protect outbound DNS and IP traffic to prevent attacks in their track.
- Significant Attack Surface Reduction
- Out-of-Box Emerging Threat Protection
- Vendor Agnostic Threat-Intelligence and Tactical Blocking
- Real-Time Adversary Behavior and ML Detection
- Continuous Response and Incident Containment

Eclipse EDR
To establish trust in the IT environment for the board and executives, CyberStash conducts forensic-level analysis across the entire IT fleet at a frequency defined by the organization’s risk appetite.
CyberStash obtains a higher degree of resilience and assurance by forensically detecting and responding to compromised systems and discovering previously undetected breaches before they can cause irreversible damage.
With the ability to uncover compromised hosts within 1 day, CyberStash reduces the likely occurrence of actual business impact by 96%
- Collection of Forensic-Level System Information
- Forensic Depth Analysis
- Enrichment using Code Comparison, Machine Learning, Sandboxing & Threat Intelligence
- Conclusively Confirm Endpoints as Compromised to Establish Trust
- Assurance of Malware and Human Adversariy Eradication


The Results
Block Attacks at Scale
Significantly reduces the likelihood of a breaches.
Detect Breaches that Evade Defenses
Reduces the likelihood of major business impacts.
Deliver Comprehensive Insights Into the Threat Landscape
Continuously reduces exposure to actual and potential attacks.
Optimise Risk Management and Resources
Continuously respond to threats at scale leveraging automation and orchestration.
100,000+
Hours of Detection & Response
150,000+
Endpoints Surveyed
120+
Clients Protected
The team at CyberStash provide us with peace of mind and excellent service offerings. They have never failed to respond to any query. Solid and reliable, always willing to go an extra mile when asked for help. A true value addition to our team.









