SSH Communications Security
Inventor and Origin of Secure Shell – and Beyond.
For Humans, Systems, and Networks.
SSH provides defensive cybersecurity solutions and related services for critical and sensitive data in use, in transit, and at rest. SSH deliver security based on the Zero Trust principle: Never Trust – Always Verify.
SSH focus on high-impact users that represent a tiny part of all users and a major part of the cyber risk exposure. They find and secure critical automated connections – and give them an identity.
When a ship in the ocean needs remote diagnostics, a credit card database is updated, an acquisition project must remain a secret, an electricity grid requires on-site adjustment, or your personal health or financial data is in transit – you can defend them against threats, hacks, and credential misuse.
Helping
- Defensive Cybersecurity
- Quantum-Safe Encryption
- Passwordless Environments
- Keyless Deployments

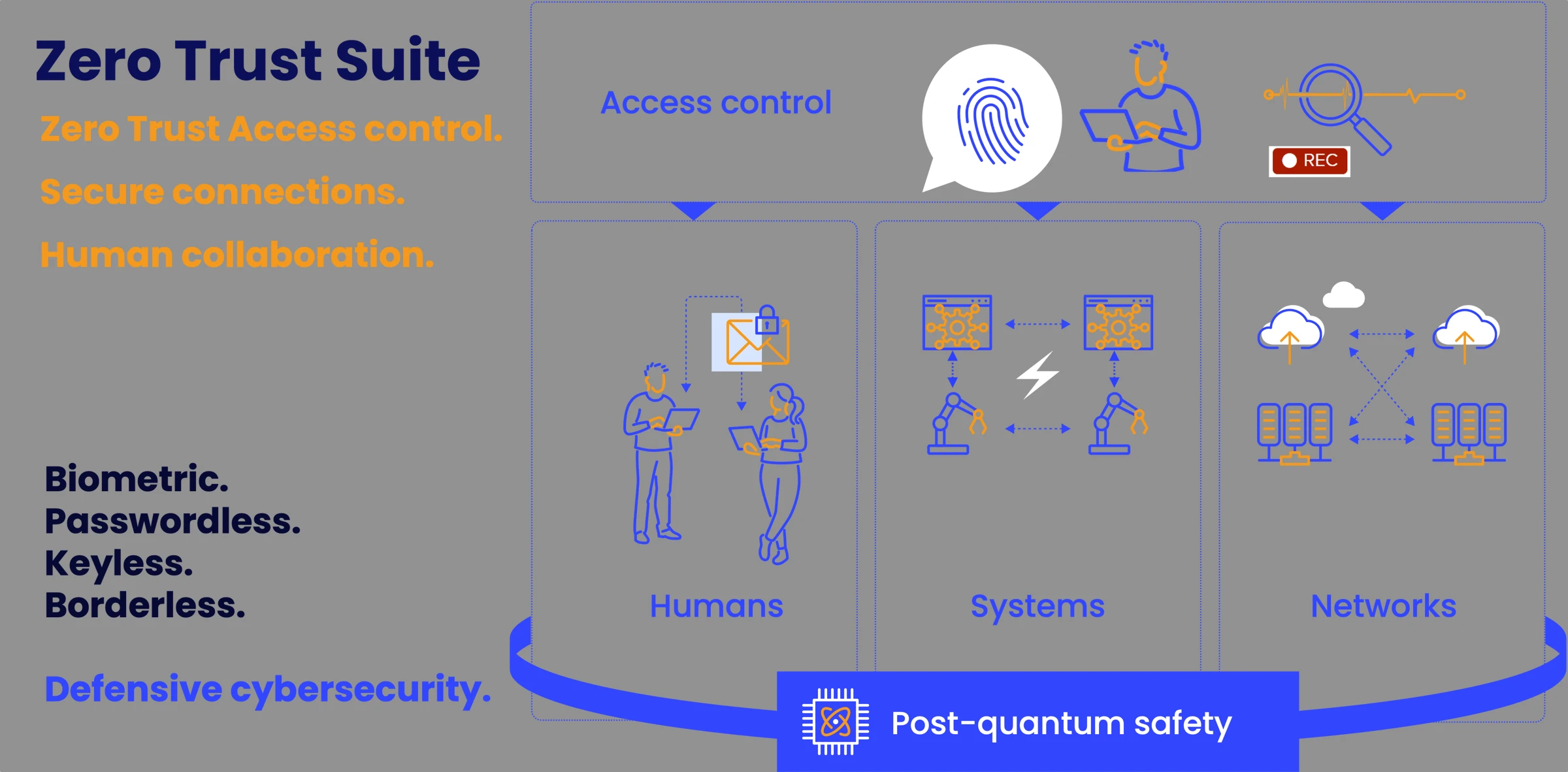
Zero Trust
PrivX Zero Trust Suite for Secure Critical Communications
SSH Zero Trust Suite is a modular software suite that allows companies to communicate securely in traditional on-premise environments, when migrating to the cloud – and at any stage in between. It works well in IT, industrial OT and multi-protocol environments.
The Suite secures communications up to a quantum-safe level when:
- Applications, systems, sites, machines or data centers need to connect
- Humans share sensitive data with each other
- Experts need to access critical targets for updates, production environment uploads, maintenance or configurations
- Identify. Restrict. Authorize. Control.
- Audit. Monitor. Record.
- Integrate with your existing security architecture
- Protect on-prem, hybrid, and cloud environments alike
- Share, transmit, and store sensitive information securely
- Identify and secure automated connections
- With or without permanent credentials. You choose.
- Secure your future with quantum-safe connections
SSH Zero Trust Key Management
PrivX PAM
Tectia File Sharing and Tunneling
SSH Secure Collaboration 2024
Quantum Safe
Quantum-Safe Cryptographic Security Solutions
Defend your long-term secrets against the quantum threat with quantum-safe cryptography (QSC) and quantum security solutions.
Quantum computers already exist and their power is increasing. Soon, they will reach the point where classical cryptography is in danger.
With more sophisticated quantum computing technology, all data encrypted with classic encryption is vulnerable. Encrypted traffic is already being captured and recorded – eventually, it will be possible to unlock the traffic when large-scale quantum computers will exist.
SSH focus on securing:
- Critical networks that are based on IPSec and SSH
- Environments where you cannot upgrade the hardware
- Connections difficult to upgrade using in-house skills
- Large-scale data transmissions
- Long-term and sensitive secrets
NQX
PrivX PAM
Tectia Client/Server
Post-quantum security for your file transfers, application-to-application (A2A), machine-to-machine (M2M), and secure remote access.
PrivX Key Manager

NQX
NQX™ QUANTUM-SAFE ENCRYPTOR
High performance,quantum-safe data transmissions
SSH NQX™ transmits large-scale data using future-proof quantum-safe algorithms at speeds up to six times faster than competition.
- Adapts to your security needs with crypto agility
- High performance, high speed with PQC
- Flexible & adaptable
- Operational efficiency
- Install and deploy fast
- Certified for the transport of classified data
What makes NQX quantum-safe?
- NQX uses quantum-safe encryption and authentication algorithms
- NQX comes with key exchange support hardening to mitigate against quantum threats
- NQX is software-based to enable easy, fast and cost-effective future transition to post-quantum cryptography (PQC) algorithms
- NQX is upgradeable to Post-Quantum Cryptography (PQC) Edition
- The Utility data plane is protected from Quantum Threat using non-scaleable technologies
- NQX PQC Edition is protected from the Quantum Threat using a new set of algorithms that are believed to be hard to crack for Quantum Computers
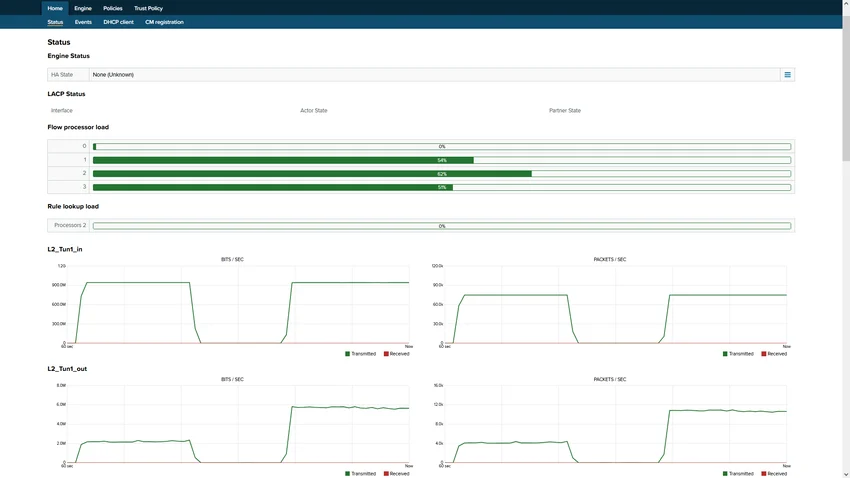
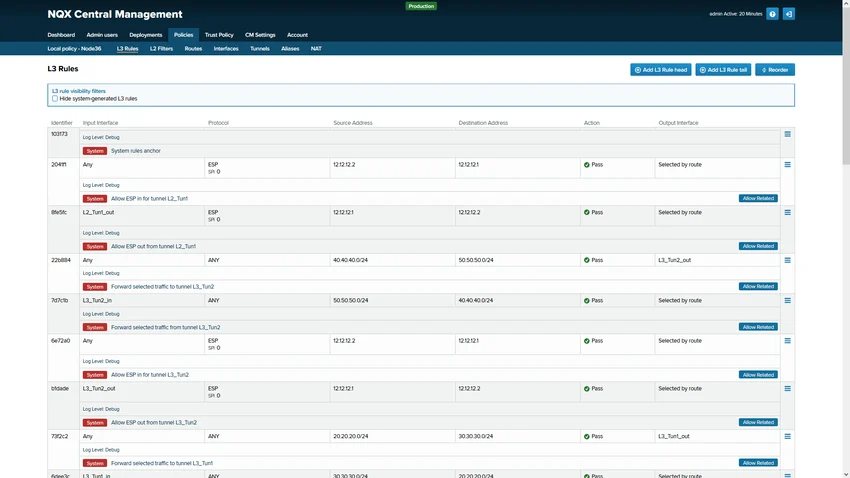
OT Security
SSH OT offering fulfills NIST CSF 2.0 requirements
Our comprehensive OT security offering covers four out five main categories of the National Institute of Standards and Technology Cybersecurity Framework 2.0.
- Identify
- Protect
- Detect
- Respond
PRIVX OT™
Centralise on- and off-site secure access management to any OT/IT target with our cost-efficient software solution.
BEYONDIDENTITY & SSH
Apply strong biometric authentication for critical access and validata the security posture of the device throughout the session.
HONEYWELL FORGE & SSH
Discover your ICS/OT assets, detect anomalous behaviour and secure access to targets.
NQX™
Transmit vast amounts of data quantum-safely, at scale, and at high speeds between networks, clouds, data centers, or industrial sites.
- The PrivX OT solution can be deployed on-site or as a shared instance across multiples sites or regions to a public or private cloud.
- The base of access is identity.
- Named users who are tied to the HR processes are imported to PrivX OT.
- The solution can integrate to any number of identity solutions.
- Or site-specific or local identity source giving controlled access to a wide range of employee identities
- The users are imported and mapped to roles – continuously .
- PrivX OT hosts the site’s required access topography as a role structure. Examples:
- Production management roles access ERP
- Plant control oversees the production across multiple processes
- Process-specific roles granting access the supervisory or control roles
- 3rd party contractors are given just-in-time and time-boxed temporary access to specific resources
- without bringing the contractors to the organizational identity source
- letting contractors install their own proprietary connectivity solutions
- Usually, operational management stations in level 3 which provide secure access to control & monitor processes on lower levels.
- PrivX OT can be deployed outside the site and still reach destinations within the site to make the private, protected networks accessible.
- PrivX OT supports various mechanisms to authenticate to access management solution, including:
- standard identity provider SSO
- client certificates
- passkeys
- biometric authentication
- and more
- The connections can be audited, restricted to happen during working hours or from specific source addresses. The authentication to the target systems can happen via passwords, keys or passwordless, ephemeral access.
- With role based network access, log in to PrrivX OT and request routed network level access to a target system which enables them to use various OT protocols.
- PrivX OT can monitor for PAM bypassing connections and detect threats or vulnerabilities within the OT network.
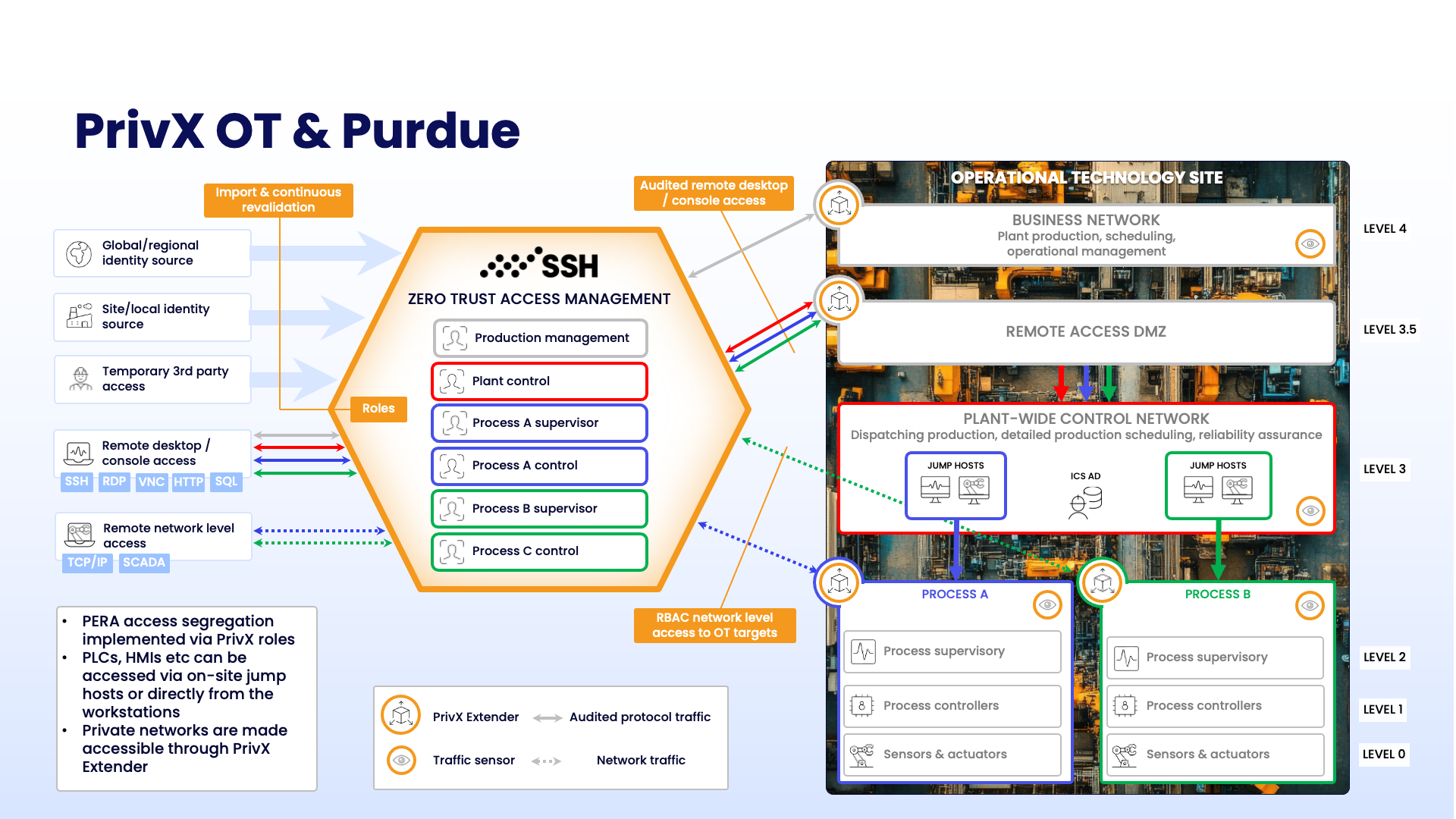
Problems Solved
Keeping critical and sensitive data safe.
In use, in transit, and at rest.
Zero Trust
- Just-in-Time (JIT) and Just Enough Access (JEA) each session.
- Get policy reports for compliance.
- Discover assets, continuously monitor their security posture.
- Device Trust, non-phisable authentication.
Privileged Access Management (PAM)
- Link IDs to roles.
- Protect, audit and monitor privileged users.
- For IT/OT/MSP environments.
- Scalable, high-performing and comprehensive PAM.
Crypto-Agility and Quantum Safeness
- Use classical and post quantum cryptography (PQC) in parallel.
- Upgrade to new quantum-safe encryption as it becomes available.
- Easy, software-based migration.
Secrets and Key Management
- Manage, vault and rotate passwords, keys and other secrets.
- Just-in-time (JIT), Zero Trust access.
- Migrate to passwordless and keyless authentication.
File transfers & patch management
- Secure remote file & patch uploads and downloads.
- Protect against malware payloads.
- Manage session permissions.
Network security
- Secure critical large-scale transmissions.
- Between systems and data centres.
- Transmit data at deeper layers (L2 or L3) of network.
Secure Collaboration
- Secure sensitive emails, video conferences, messages and chats.
- For compliance and record-keeping.
- A data sovereign solution.
OT Security
- Protect critical infrastructures, ICS/OT targets and production sites.
- Locally, globally on on-site.
- Fast, secure and safe access at scale.